Silent renew always fails with login_required
See original GitHub issueI have a small sample based on the PKCE blog post and the accompanying project.
I can upload place the code somewhere for review, but the only changes are:
- I switched to using the NPM library.
- I removed the translation bits to yield a simpler demo.
- My secure files component only shows a piece of text, also to make it simpler.
- I’m reading the config values from a JSON files, not an extra web service. Again, for the sake of simplicity.
I’m connecting to an IdentityServer4 authority, which uses Azure AD to authenticate.
When I sign in, everything looks good and I’m authenticated, I get a token, and userinfo is called and returns sensible results.
Then I see the silent renew entries. They all look something like this:
onCheckSessionChanged
app.component.ts:36 ...recieved a check session event
angular-auth-oidc-client.js:337 silentRenewHeartBeatCheck
silentRenewRunning: false
idToken: true
_userData.value: true
angular-auth-oidc-client.js:337 Token not expired?: 1580881666000 > 1580881646545 (true)
angular-auth-oidc-client.js:337 <iframe id="myiFrameForCheckSession" style="display: none;">…</iframe>
angular-auth-oidc-client.js:337
Until the token expires:
...recieved a check session event
angular-auth-oidc-client.js:337 silentRenewHeartBeatCheck
silentRenewRunning: false
idToken: true
_userData.value: true
angular-auth-oidc-client.js:337 Token not expired?: 1580881666000 > 1580881667564 (false)
angular-auth-oidc-client.js:337 IsAuthorized: id_token isTokenExpired, start silent renew if active
angular-auth-oidc-client.js:337 BEGIN refresh session Authorize
angular-auth-oidc-client.js:337 RefreshSession created. adding myautostate: 15808816675640.<Redacted>
angular-auth-oidc-client.js:337 startRenew for URL:https://<redacted>.azurewebsites.net/connect/authorize?client_id=MyClientID&redirect_uri=https%3A%2F%2Flocalhost%3A4200%2Fassets%2Fsilent-renew.html&response_type=code&scope=openid%20profile%20api1&nonce=N<Redacted>&state=<Redacted>&code_challenge=<Redacted>&code_challenge_method=S256&prompt=none
angular-auth-oidc-client.js:337 silentRenewEventHandler
app.component.ts:75 Auth result received AuthorizationState:unauthorized validationResult:LoginRequired
app.component.ts:81
I redacted state, nonce and code and anything else I thought migh be sensitive, but they all look like I’d expect.
Notice that the silent renew sends prompt=none, which is what I expect. IdentityServer responds with login_required.
Looking at the IdentityServer logs, I see this for the intial (interactive) login:
IdentityServer4.Endpoints.AuthorizeCallbackEndpoint: ValidatedAuthorizeRequest
{
"ClientId": "RegisteredClientID",
"ClientName": "My App Name",
"RedirectUri": "https://localhost:4200/auth-callback",
"AllowedRedirectUris": [
"https://localhost:4200/auth-callback",
"https://localhost:4200",
"https://localhost:4200/assets/silent-renew.html"
],
"SubjectId": "253aa016-74ed-40dc-8b78-5aa5085a4df6",
"ResponseType": "code",
"ResponseMode": "query",
"GrantType": "authorization_code",
"RequestedScopes": "openid profile api1",
"State": "<Redacted>",
"Nonce": "N<Redacted>",
"SessionId": "<Redacted>",
"Raw": {
"client_id": "RegisteredClientID",
"redirect_uri": "https://localhost:4200/auth-callback",
"response_type": "code",
"scope": "openid profile api1",
"nonce": "N<Redacted>",
"state": "<Redacted>",
"code_challenge": "<Redacted>",
"code_challenge_method": "S256"
}
}
The silent renew fails every time:
IdentityServer4.Endpoints.AuthorizeEndpoint:
{
"ClientId": "MyRegisteredClientID",
"ClientName": "My App Name",
"RedirectUri": "https://localhost:4200/assets/silent-renew.html",
"AllowedRedirectUris": [
"https://localhost:4200/auth-callback",
"https://localhost:4200",
"https://localhost:4200/assets/silent-renew.html"
],
"SubjectId": "anonymous",
"ResponseType": "code",
"ResponseMode": "query",
"GrantType": "authorization_code",
"RequestedScopes": "openid profile Citadel.Auth",
"State": "<Redacted>",
"Nonce": "N<Redacted>",
"PromptMode": "none",
"Raw": {
"client_id": "MyRegisteredClientID",
"redirect_uri": "https://localhost:4200/assets/silent-renew.html",
"response_type": "code",
"scope": "openid profile Citadel.Auth",
"nonce": "N<Redacted>",
"state": "<Redacted>",
"code_challenge": "<Redacted>",
"code_challenge_method": "S256",
"prompt": "none"
}
}
This causes a Token Issued Failure error with login_required.
Note that it sends along the code, but not the subject, and not the session ID. This seems intuitively correct to me, as the session is expired (that’s why we’re renewing) and the code was issued to refresh the session, so it should surely imply the subject. But clearly my intuition is way off.
Here is the error showing the token issue failure:
IdentityServer4.Events.DefaultEventService: {
"Name": "Token Issued Failure",
"Category": "Token",
"EventType": "Failure",
"Id": 2001,
"ClientId": "MyRegisteredClientID",
"ClientName": "My App Name",
"RedirectUri": "https://localhost:4200/assets/silent-renew.html",
"Endpoint": "Authorize",
"Scopes": "openid profile api1",
"GrantType": "authorization_code",
"Error": "login_required",
"ActivityId": "80000980-0000-bc00-bf76-84710c7967bb",
"TimeStamp": "2020-02-05T05:31:09Z",
"ProcessId": 90786,
"LocalIpAddress": "<Redacted>",
"RemoteIpAddress": "<Redacted>"
}```
Issue Analytics
- State:
- Created 4 years ago
- Comments:9 (3 by maintainers)
 Top Related StackOverflow Question
Top Related StackOverflow Question
Hello if anyone has the same issue with asp.net core here is what i ve done. I don’t recommand what i did in production, i’am still in the process of understanding and tightening the security. 1- Allow the cookie to be available ( Cross Site Request Forgey )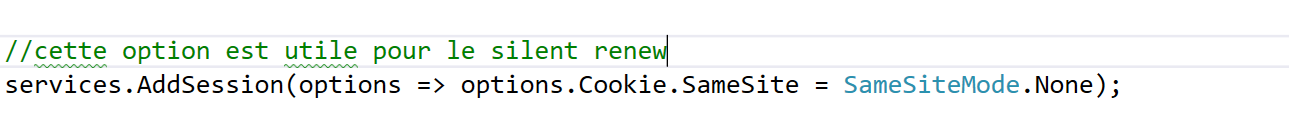
2- Allow the site to be available within iframe
3- Make sur you are on the same browser and not in private mode . i made my angular app available through https so that it can run on another tab of the same chrome instance.
I have the similar issue after adding the second client. I explain in here https://github.com/damienbod/angular-auth-oidc-client/issues/1413 My subject id also null like @CobusKruger